Timeline
Back to: Introduction to CyberSecurity
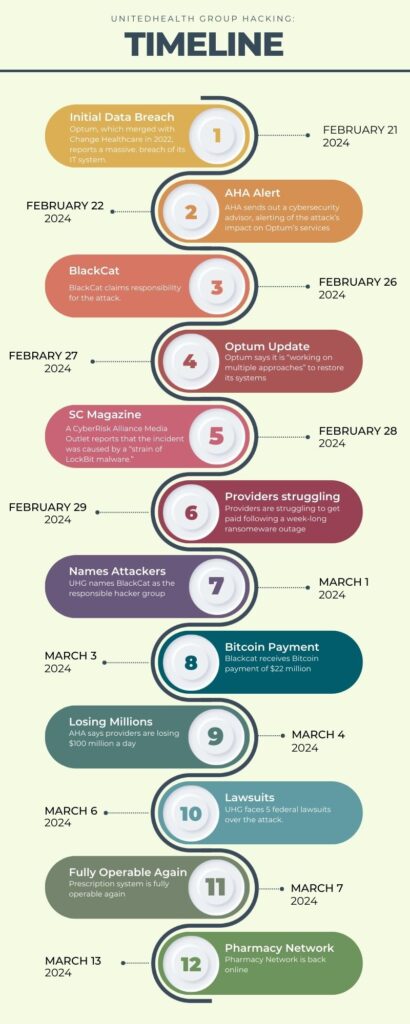
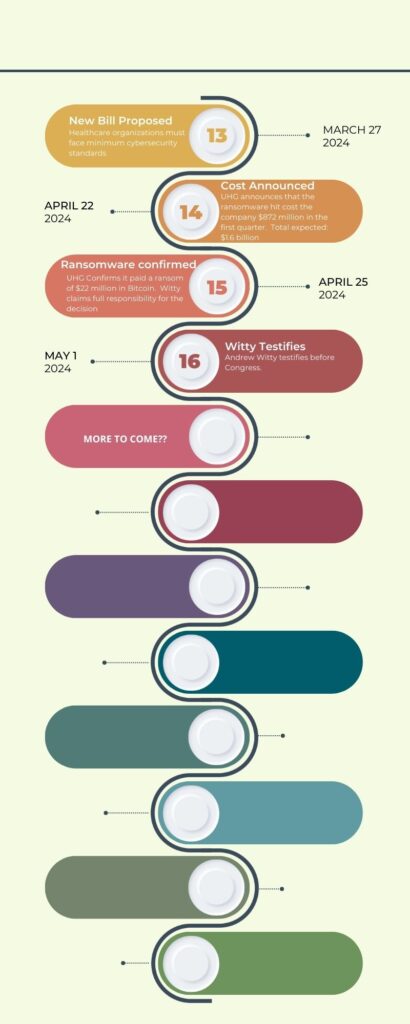
What Is LockBit Ransomware?
LockBit ransomware has been implicated in more cyberattacks this year than any other ransomware, making it the most active ransomware in the world. And while the average ransomware payment is nearly $1 million per incident, LockBit victims pay an average ransom of approximately $85,000—indicating that LockBit targets small-to-medium-sized organizations.
LockBit was first observed in September 2019. Since then, it has evolved: LockBit 2.0 appeared in 2021; LockBit 3.0, the current version, was discovered in June 2022.
LockBit seeks initial access to target networks primarily through purchased access, unpatched vulnerabilities, insider access, and zero-day exploits. “Second-stage” LockBit establishes control of a victim’s system, collects network information, and achieves primary goals such as stealing and encrypting data.
LockBit attacks typically employ a double extortion tactic to encourage victims to pay, first, to regain access to their encrypted files and then to pay again to prevent their stolen data from being posted publicly. When used as a Ransomware-as-a-Service (RaaS), an Initial Access Broker (IAB) deploys first-stage malware or otherwise gains access within a target organization’s infrastructure. They then sell that access to the primary LockBit operator for second-stage exploitation.